Jim Rohn once famously said, “Without a sense of urgency, desire loses its value.” Resilience is key to surviving in today’s world full of emerging technologies and hot-button buzzwords. It is a race towards all that is good, towards cyber survivability, a race of the utmost urgency and importance. As such, cybersecurity and, in particular, cyber resiliency is more than just having an incident response plan or a computer security policy. It is about ensuring that your entire security posture can withstand a wide range of threats, which includes hybrid, blended attack vectors that can transcend time and space through the interplay of physical, cyber, and virtual planes that take apart traditional brick-and-mortar aspects of any organisations and cross-borders jurisdiction.
Hence, we need to design a more holistic security framework by integrating cyber and physical security measures, hardening critical systems, and creating cross-functional teams and multi-disciplinary teams that will involve team members not only from our own organisation but also from other stakeholders in our ecosystem that can address risks from multiple angles. Indeed, designing an auto-adaptable, self-evolving security framework that will evolve alongside the volatile and rapidly evolving threat landscape will be crucial to maintaining cyber resiliency and, therefore, safeguarding the business in the new intelligent era. But, without a doubt, there’s an urgent need to prioritise building cyber resiliency above all other matters.
Leonardo Da Vinci said, “I have been impressed with the urgency of doing. Knowing is not enough. We must apply. Being willing is not enough. We must do.” To build resilience, having a lofty mission statement with an ambitious plan is definitely not enough; the efforts must be grounded in the practicality of getting our hands dirty and being able to paddle in and out of the mudflats regardless of how much the mud will engulf you.
Figure 1 shows our proposed RACE model as a simple four-part process to look at how organisations can build cyber-resiliency with a feasible and actionable plan to achieve our objective of securing any organisation by going back to basics. By going back to basics and doing them well, it will at least address 90% of the problems that most organisations are facing today. The solution needs not to be complex nor flamboyant; it just needs to be practical, and if one can cut through the levels of complexity and zero in on the crux of the problem and put in place basic security controls that are effective and efficient, it will lay the groundwork for success.
Borrowing the analogy of racing, would you be driving a race car that has a manual gearbox for full control and is tuned for the race track, or would you just take any car straight from the garage untuned for the conditions of the race track and relying on the car’s automatic gearbox to take care of the driving? Thus, it is clear that returning to basics and tuning your security measures for accuracy and precision is a much better bet than pouring huge investments into advanced systems and mechanics, building layers and layers of security indiscriminately.
Being accurate and precise will enable us to build quantifiability into our cybersecurity programme. Accuracy and precision are both ways to measure results. Accuracy measures how close results are to the true or known value, while precision, on the other hand, measures how close results are to one another or, in other words, how well our defenses are designed and executed. This is our motivation behind the development of the RACE model. The subsequent paragraph will describe each key component of the model in greater detail.
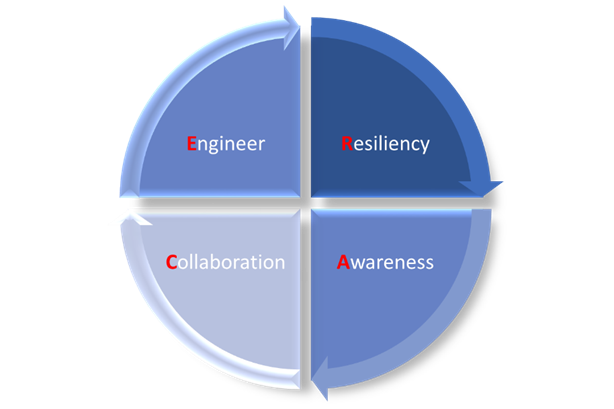
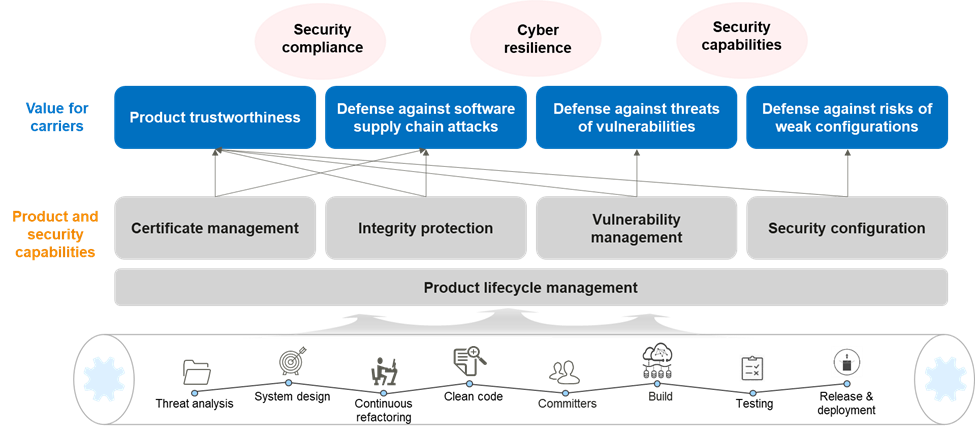
Firstly, resiliency in modern cybersecurity speaks to the capability to provide value for the customer. In simplistic terms, it is to provide robustness and survivability of the organisation’s cyber footprint in the face of adversaries and threats, meet compliance needs for business governance while excelling and providing a competitive advantage, using whatever security capabilities are based on established best practices, processes, and frameworks that achieve repeatable results. Figure 2 below summarises what it takes to build cyber resilience and the value it brings to the table, taking into consideration the interplay between being compliance and building capabilities to support the resiliency of the entire information infrastructure that supports the business of an organisation.
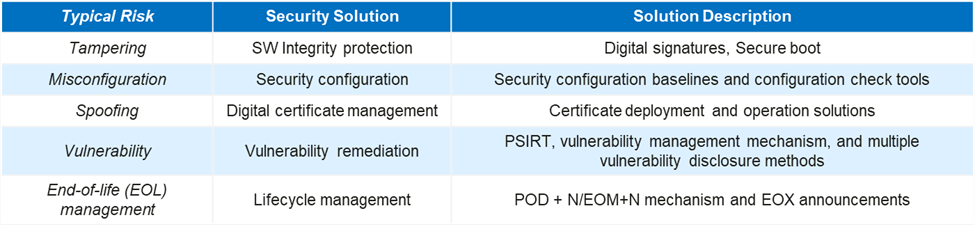
Next, awareness refers not only to imbuing a culture of cybersecurity among all the staff in an organisation to the extent that basic cyber hygiene can be practiced but also to targeting the team focusing on delivery and maintaining ICT and security services within the organisation so that they pay attention to cementing their core competencies and fundamentals. Hereby, it is recommended that harnessing risks and hedging your bet against the barrage of threats based on a risk-based approach is the best way, given that resources on hand are always scarce, limited, and, to some extent, expensive. Given that is the case, we have identified five basic core fundamentals that every cybersecurity team in any organisation needs to build up on their basics (and manage them well) based on common cybersecurity issues faced, as depicted in Figure 3. While it may seem simple, the devil is always in the details to ensure a job is done well.
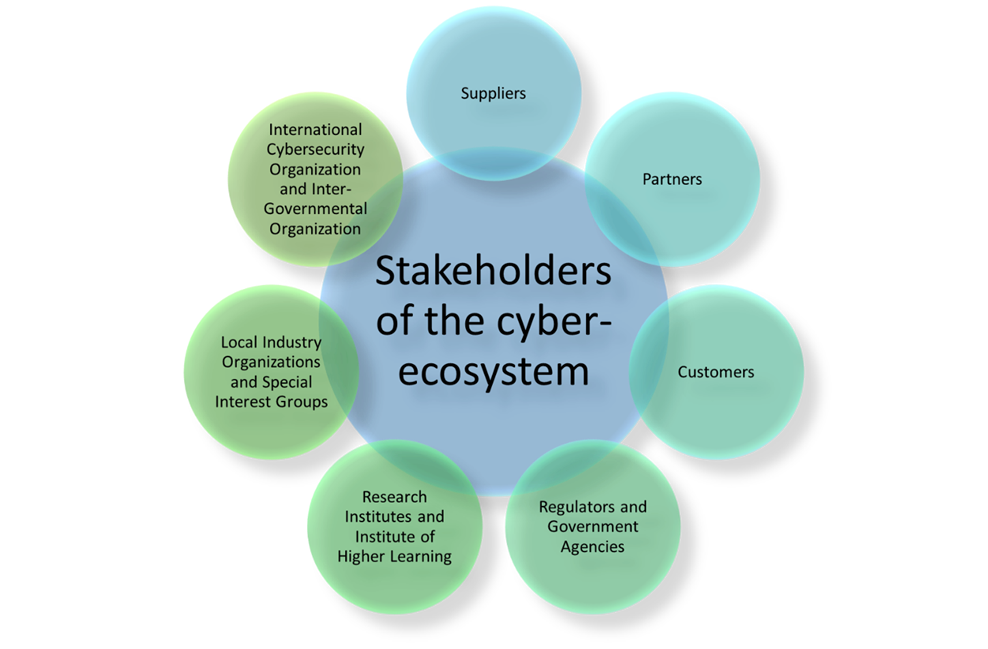
One man, organisation, or country cannot resolve cybersecurity issues alone. It takes an entire village to address cybersecurity issues as they affect everyone if anything goes awry. Cybersecurity is a team sport, and all the stakeholders within the ecosystem must contribute towards addressing the elephant in the room, as shown in Figure 4. We always find strength in numbers because “united we stand, divided we fall.” We see the Blackhat community is doing that exactly, and that is why they are always a step ahead of the good guys every time, thereby summarising the urgency to Collaborate as a key differentiating measure.
Last but not least, we need to bring everything together to build or Engineer the process, putting the cogwheels into their rightful places to drive the engine forward. We have identified five key fundamental security measures that, if done diligently, will be key to building an end-to-end resilient system and reducing network risks.
As shown in Figure 3, the five key fundamental security measures are 1) software integrity protection, 2) security configuration, 3) digital certification management, 4) vulnerability remediation, and 5) product lifecycle management. Take “Security configuration” as an example. To engineer and address the risk brought about by system misconfiguration, we need to break it down into its elements or identify its Work Breakdown Structure or WBS, which is a key step for planning project tasks and allocating resources.
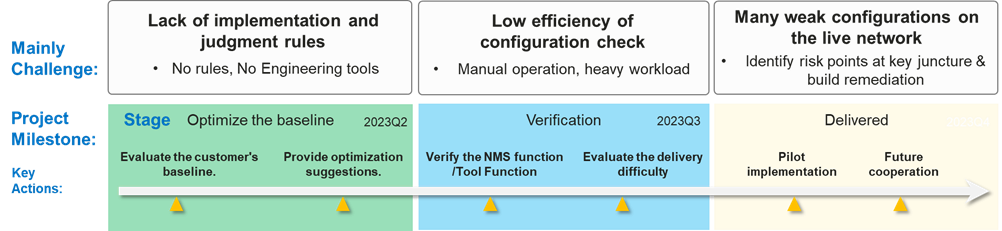
Figure 5 summarises typical work done to break down “security configuration” into its WBS. While this figure does not depict the complete picture, it does show a deep dive into each piece of work. One should keep working on breaking it down until the project scope and all the tasks required to complete the project can be visualised in one snapshot.
In conclusion, we have distilled the entire RACE model in detail in this paper. Achieving RACE is key to building resiliency for any organisation. The important thing to note is to keep it simple and go back to basics. Build an auto-evolving, adaptable security framework based on the strategy that is designed to shape-shift alongside emerging blended, hybrid threats by leveraging on actionable intelligence, building resilience, and fostering collaboration so that individuals, organisations, and nations. Establishing public-private partnerships (PPP) with governmental entities and authorities enables public sector players, such as the UAE Cyber Security Council, to act as the fulcrum for coordinating and pooling resources and intelligence. This will enable our modern society to defend against today’s threat and safeguard one’s digital journey by addressing the challenges of tomorrow’s Age of Intelligence.








Discussion about this post