Kaspersky’s GReAT team has uncovered a sophisticated new Lazarus campaign, combining a watering hole attack with the exploitation of vulnerabilities in third-party software to target organisations in South Korea. During the research, company experts have also discovered a zero-day vulnerability in the widely used South Korean software Innorix Agent, which was promptly patched. Revealed during GITEX Asia, the findings highlight how Lazarus, leveraging its deep understanding of South Korea’s software ecosystem, is capable of executing highly sophisticated, multi-stage cyberattacks.
According to a new report from Kaspersky GReAT (Global Research and Analysis Team), the attackers targeted at least six organisations across the software, IT, financial, semiconductor, and telecommunications sectors in South Korea. However, the actual number of victims may be higher. Kaspersky researchers have dubbed this campaign “Operation SyncHole”.
The Lazarus Group, active since at least 2009, is a well-resourced and notorious threat actor. In a recent campaign, the group was observed exploiting a one-day vulnerability in Innorix Agent, a third-party browser-integrated tool used for secure file transfers in administrative and financial systems. By exploiting this vulnerability, the attackers were able to facilitate lateral movement, enabling the installation of additional malware on a targeted host. This ultimately led to deployment of Lazarus signature malware, such as ThreatNeedle and LPEClient, which expanded their foothold within internal networks. This exploit was part of a larger attack chain, delivered via the Agamemnon downloader, and specifically targeted a vulnerable version of Innorix (9.2.18.496).
While analysing the malware’s behavior, Kaspersky’s GReAT experts discovered another additional arbitrary file download zero-day vulnerability, which they managed to find before any threat actors used it in their attacks. Kaspersky has reported issues in Innorix Agent to the Korea Internet & Security Agency (KrCERT) and the vendor. The software has since been updated with patched versions, while the vulnerability was assigned with the KVE-2025-0014 identifier.
“A proactive approach to cybersecurity is essential, and it was thanks to this mindset that our in-depth malware analysis uncovered a previously unknown vulnerability before any signs of active exploitation appeared. Early detection of such threats is key to preventing broader compromise across systems,” comments Sojun Ryu, security researcher at Kaspersky’s GReAT (Global Research and Analysis Team).
Prior to findings related to INNORIX, Kaspersky experts had previously discovered the use of a variant of the ThreatNeedle and SIGNBT backdoor in subsequent attacks against South Korea. The malware was running in the memory of a legitimate SyncHost.exe process, and was created as a subprocess of Cross EX, legitimate South Korean software designed to support the use of security tools across various browser environments.
The detailed analysis of the campaign confirmed that the same attack vector was consistently identified in five more organisations in South Korea. The infection chain in each case appeared to originate from a potential vulnerability in Cross EX, suggesting it was the starting point of the infection within the entire operation. Notably, a recent security advisory published by KrCERT confirmed the existence of a vulnerability in CrossEX, which has since been patched during the timeframe of this research.
“Together, these findings reinforce a broader security concern: third-party browser plugins and helper tools significantly increase the attack surface, particularly in environments that rely on region-specific or outdated software. These components often run with elevated privileges, remain in memory, and interact deeply with browser processes, making them highly attractive and often easier targets for attackers than modern browsers themselves,” comments Igor Kuznetsov, Director of Kaspersky’s GReAT (Global Research and Analysis Team).
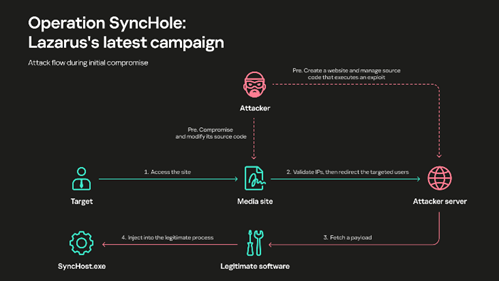
How Operation SyncHole attacks begin
The Lazarus Group used compromised online media websites typically visited by large numbers of users as lures — the technique is known as watering hole attacks. The threat actors filtered incoming traffic to identify individuals of interest, selectively redirecting those targets to attacker-controlled websites where a series of technical actions initiated the attack chain. This method highlights the highly targeted and strategic nature of the group’s operations.

To learn more about Lazarus’ latest campaign, visit Securelist.com
Kaspersky products detect the exploits and malware used in this attack with the following verdicts: Trojan.Win64.Lazarus.*, Trojan.Win32.Lazarus.*, MEM:Trojan.Win32.Cometer.gen, MEM:Trojan.Win32.SEPEH.gen, Trojan.Win32.Manuscrypt.*, Trojan.Win64.Manuscrypt.*, Trojan.Win32.Zenpak.*
To defend against Lazarus and other Advanced Persistent Threat (APT) attacks, Kaspersky recommends accurate detection, rapid response to known tactics, and prompt remediation of vulnerabilities. Additional advice includes:
- Always keep software updated on all the devices you use to prevent attackers from infiltrating your network by exploiting vulnerabilities.
- Carry out a cybersecurity audit of your networks and assets to reveal gaps and vulnerable systems, and address any weaknesses discovered in the perimeter or inside the network.
- To protect the company against a wide range of threats, use solutions from the Kaspersky Next product line that provide real-time protection, threat visibility, investigation and response capabilities of EDR and XDR for organisations of any size and industry
- Provide your InfoSec professionals with an in-depth visibility into cyberthreats targeting your organisation. The latest Kaspersky Threat Intelligence will provide them with rich and meaningful context across the entire incident management cycle and helps them identify cyber risks in a timely manner.









Discussion about this post