How To Manage Email Phishing Risks
Marcus Troiano and John Atrache from FireEye discuss how organisations can navigate and contain the increasing number of security risks that remote working brings to the forefront.

There are viruses, and then there are viruses. COVID-19 has rapidly taken over the headlines, with countries, organisations, and individuals scrambling to contain the virus, and maintain some level of normalcy in daily life. Borders are closed, international travel is at a standstill, and most major employers are having their workforces work remotely. Remote work introduces many Business Continuity and Disaster Recovery challenges. From a cyber perspective, organisations need to be on the lookout for two escalating risks brought about by this evolving event: firstly, the large increase of phishing and social engineering campaigns that use public fear to enhance their effectiveness, and secondly the increased risks due to users working from home en masse. FireEye recently published a blog post which covers off this latter risk.
When it comes to risks related to social engineering and phishing, attacks leveraging COVID-19 represent a heightened risk of cyber attack to organisations worldwide, regardless of industry. As early as February 2020, and with increased frequency since then, Mandiant Threat Intelligence has observed threat actors aligning with the COVID-19 topic for their campaigns – for financial crime, cyber espionage and information operations purposes.
Private sector organisations are coming under increasing attack by financially motivated threat actors seeking to exploit their sense of urgency, fear, goodwill, and mistrust. These attackers use email to deliver malware in an effort to establish a foothold into the corporate network or siphon account credentials through phishing tactics.
Below is an example of a COVID-19 phishing email used by TEMP.Warlock threat group.
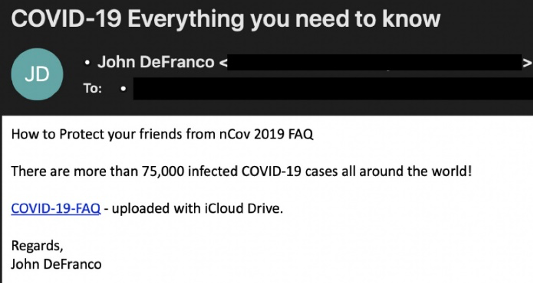
Email is a primary attack vector, and organisations must continue to focus on both building user security awareness and hardening their technical mitigative and detective controls. To enhance user awareness, organisations should communicate the risks posed by COVID-19 phishing and social engineering campaigns, providing users examples of what to watch out for and what to do if they come across such emails. Security leadership should take this opportunity to re-iterate security awareness guidance, reminding users to remain vigilant to both phishing emails and potential payment fraud scenarios. Both SANS and US CERT provide relevant guidance for increasing user awareness, which can be quickly adopted.
Beyond security awareness and training, organisations should additionally take this time to perform a review of existing email and other relevant security controls, in order to reduce the likelihood and impact of a successful phishing attack. Email-specific controls that organisations should consider implementing in the short term include, but are not limited to:
1. Enforce Multi-factor Authentication (MFA) – The importance of MFA cannot be stressed enough. Passwords alone are simply not enough to mitigate the risk of an account compromise, as users commonly re-use their credentials across services or use weak default passwords that are easily guessed by threat actors. At the very least, organisations should enforce MFA for all external access to critical assets and email services, especially from untrusted devices.
To ensure a smooth implementation of MFA, organisations should implement a consistent solution used across all services, with an enrollment process that is straight forward. The MFA implementation should rely on more secure options such as Authenticator applications instead of SMS. It is important to enable the ability for users to report MFA fraudulent requests, and to educate your users on not accepting MFA requests which they did not initiate.
Furthermore, organisations that enable MFA for email services such as Microsoft Office 365 must block legacy authentication. Legacy protocols do not support MFA, and as such, threat actors will commonly attempt to authenticate using legacy authentication to circumvent MFA and other security controls. At a minimum, legacy authentication should be blocked outside of the corporate network.
2. Configure Spoof Protection Controls – Ensure spoofing controls such as Sender Policy Framework (SPF), Domain-based Message Authentication, Reporting, and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) are fully configured for your mail-enabled domains with hard fail and reject policies, where applicable.
3. Validate Email Security Gateway Implementation – Ensure your email security gateway is fully deployed with all its advanced security capabilities. The solution should scan and block both malicious attachments and embedded URLs. In a best-case scenario, the solution should be utilising a sandbox analysis approach, rather than purely signature based. At a minimum, organisations should ensure that certain file attachment types are blocked from emails (e.g., .scr, .exe, .chm, etc.).
4. Implement Automated Email Warning Reminders – Implement mail flow rules that automatically embed an “External Email” disclaimer to each email received from an external source. The disclaimer should be used to remind users not to click on any embedded links or attachments if the sender is unknown or the email is unexpected. A sample of a mail flow rule which embeds an email header to warn users of the risks posed by external emails is shown below.
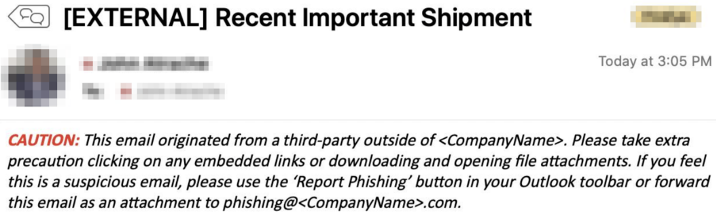
5. Formalise Phishing Reporting Process – It is important that organisations create a clear, simple, and repeatable process for their users to report phishing or suspicious emails. By having this process in place, Information Security teams are more likely to become aware of phishing campaigns and immediately investigate and contain any systems or accounts that may have been compromised as a result of users falling victim to such campaigns. Organisations should look to implement phishing reporting add-ons in their user’s email clients that auto-attach a suspicious email, and forward it to the Information Security team for further investigation.
6. Block Macros in Microsoft Office Documents – Embedded malicious macros in Microsoft Office documents continue to be a common vector used by threat actors to compromise systems. These macro-based Office documents are often attached to phishing emails or downloaded from URLs embedded within phishing emails. Organisations should consider implementing Active Directory group policy settings to “Block macros from running in Office files from the Internet”.
7. Validate Web Proxy or URL Filtering Configurations – User internet traffic should traverse a web proxy or URL filtering solution. In a best-case scenario, Internet traffic should traverse this solution whether on the corporate network or off of it (i.e., achieved using a cloud solution). Organisations should consider blocking risky websites (e.g., detected as a threat or uncategorised) or website categories in which are not relevant to the business. At a minimum, users should receive a warning page when accessing potentially risky websites. Furthermore, all files downloaded from external websites should be immediately analysed for potential threats through the use of real-time scanning and sandboxing technology.
8. Implement Strong Password Policies – Mandiant has historically observed threat actors conducting password spraying attacks. Threat actors are successful in compromising accounts due to weak password policies, allowing for the use of the “SeasonYear”, and similar variations. It is strongly recommended that organisations revise existing password policies and implement technical controls to prevent the use of weak passwords, especially for externally facing services. For organisations who have implemented Azure AD, the Azure AD Password Protection feature could potentially help achieve this.
With the large number of employees transitioning to remote work as a result of the ongoing pandemic, it is likely that there will be an increase in Help Desk support calls for password resets, MFA challenges, and other issues, and it will be important that your Help Desk personnel have a defined methodology for verifying employee identification to reduce the risk of successful social engineering attempts. For example, asking who the user’s manager is, is not a sufficient “challenge” for identity verification.
9. Ensure Sufficient Logging and Alerting is in Place – Organisations should ensure that all available logs within email services are enabled and, where possible, being forwarded to a central logging platform, and retained for an appropriate period of time. If the email service includes built-in threat detection alerting, it is recommended these features are enabled, and that alerts are either sent through the logging pipeline to a centralized dashboard, or sent to the Information Security team’s email distribution list (DL) for immediate investigation.
10. Develop and Operationalise Phishing Incident Response Playbooks – It is essential to have a consistent and comprehensive process for how to fully scope a potential phishing incident to ensure that any subsequent security incident is immediately contained (e.g., successful compromise of an account or system). This can be achieved through the development and operationalisation of an Incident Response Playbook, and should include, at a minimum, the following topics:
-
- How to review a potential phishing email
- How to securely analyse any malicious attachments or embedded URLs
- How to identify all users who have received the phishing email or other variations of the email (i.e., threat actors may use variations of subject lines or sender email accounts to circumvent common phishing email scoping techniques)
- How to validate which users fell victim to the phishing email, which includes the confirmation of accessing embedded URLs, or the download and execution of attachments
- How to immediately contain and fully investigate systems and accounts that may have been compromised as a result of the phishing incident
Implementing and enforcing the controls above is a starting point for organisations looking to quickly address the most common phishing related risks. While organisations will need to regularly reevaluate these controls to proactively adapt to the ever-changing threat landscape, a robust security awareness program remains a key defensive tactic in protecting against email-based phishing threats.





